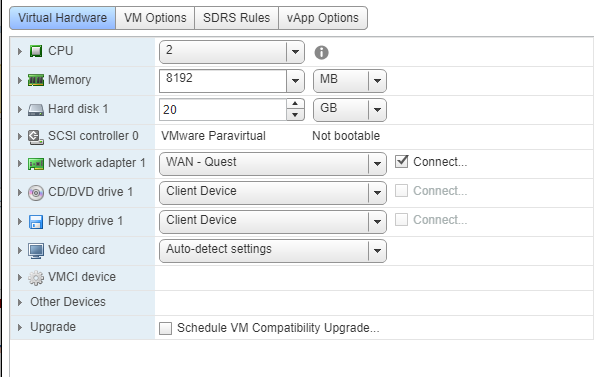
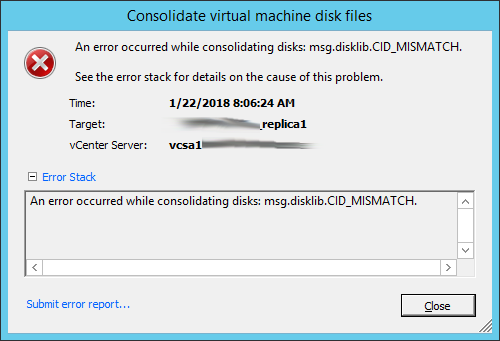
Virtual Machine Hardware Version does make a difference
For years, I have dismissed Virtual Machine Hardware version as unimportant. In fact, in this very blog, I may have advocated for leaving VM Hardware Version set at 8, to maintain full compatibility with both the vSphere C# Client and the vSphere Web Client. Unfortunately, thanks to Spectre and Meltdown, things have changed. Updating your
Read More »