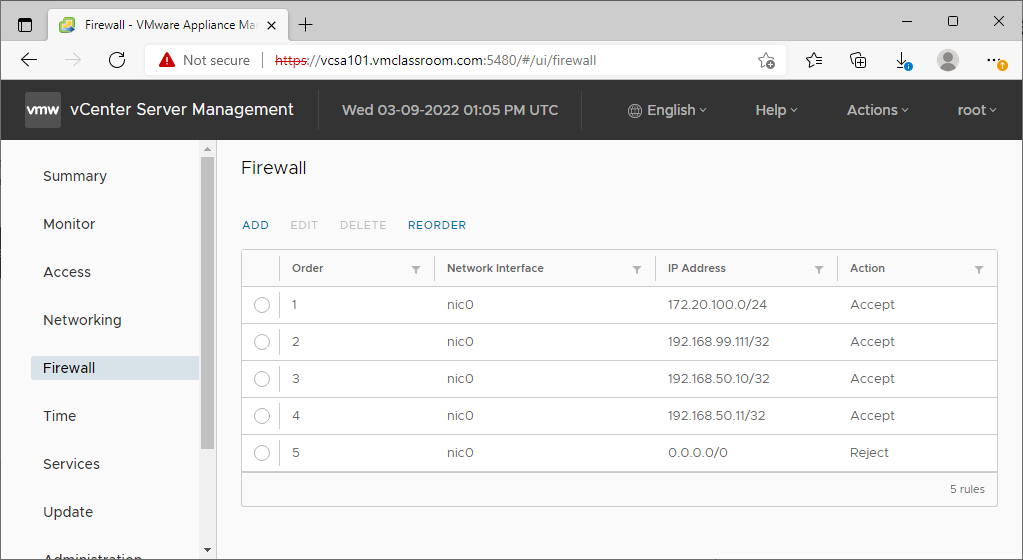
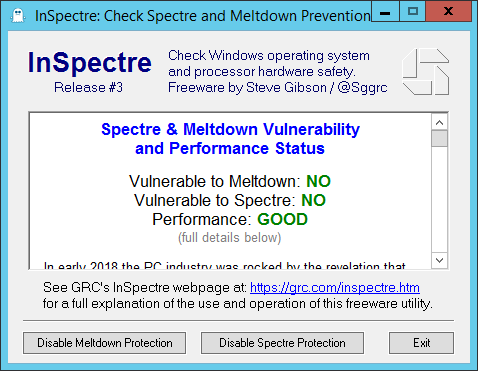
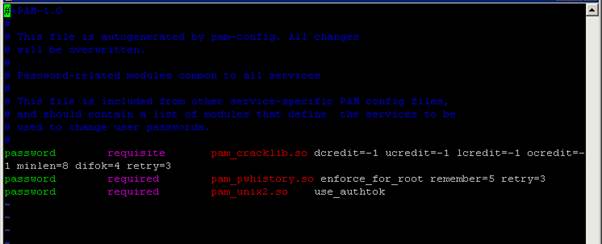
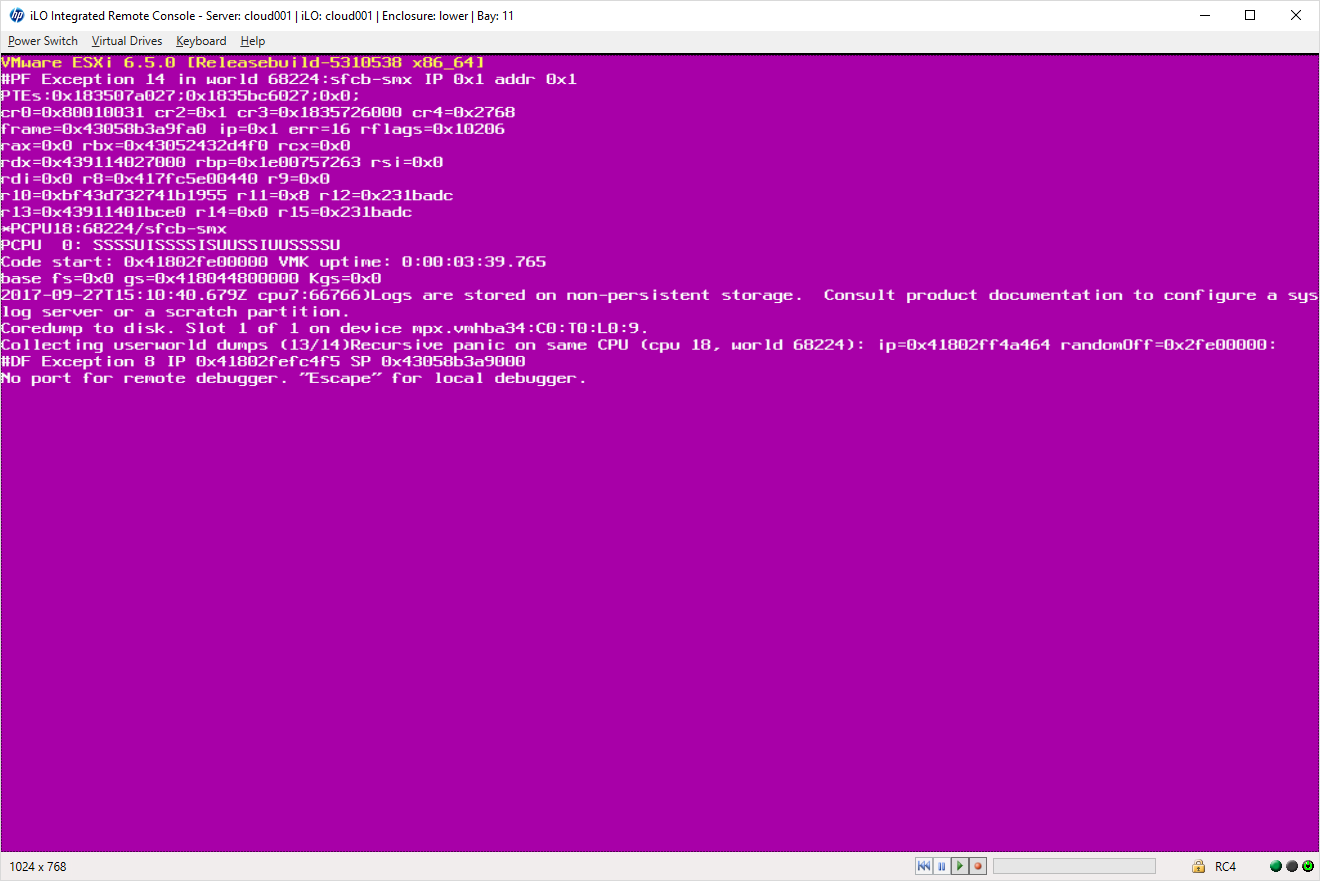
VMware vSphere Best Practices
In this post I have created a general-purpose Best Practices guideline for VMware vSphere, including references. I base these Best Practices recommendations on my personal, and VMsources collective experience, in dealing with hundreds (if not thousands, at this point) of unique client environments over the last decade. My intent is to help VMware users of
Read More »