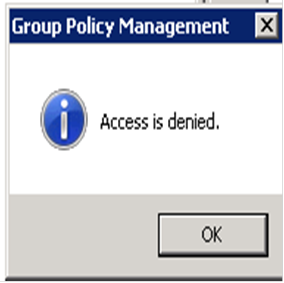
Group Policy Management Access is Denied
I spent all morning chasing an annoying error in Group Policy Management while trying to delete an old unused OU while logged in as Domain Admin: Group Policy Management Access is Denied I thought I would share the remarkably simple solution here, because I spent all morning following erroneous posts on various sites. Everyone seemed
Read More »