Patch your ESXi Hosts from the command line easily and quickly
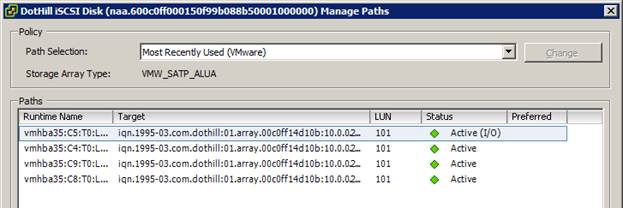
In many situations it is desirable to patch your ESXi host(s) prior to being able to install or use VMware vSphere® Update Manager™. UPDATED 4/18/2016: HP has a new URL for HP Customized VMware ISO’s and VIB’s For example: Prior to installing vCenter in a new cluster Standalone ESXi installations without a vCenter Server Hardware
Read More »