Automating vSphere Network Configuration
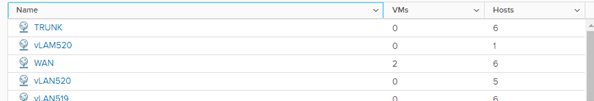
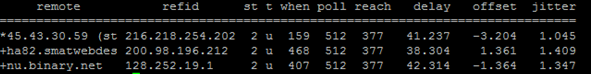
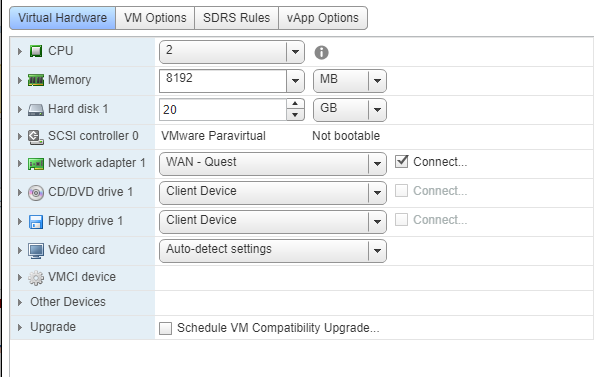
Recently I was configuring a customer’s IaaS VMware Cloud and one of the first things I noticed were some inconsistencies in the Port Group configuration across the 6 ESXi Hosts in the cluster. This is easy to see in vCenter, from the Networks view of Inventory and the Networks tab, simply compare the names of
Read More »